According to data from cybersecurity enthusiast MalwareHunterTeam, the first case of the spread of LockBit malware from the hacker group of the same name was recorded on macOS.
LockBit is an encryption program that blocks user access to the system and requires a fee for decrypting data.
In the original tweet, we are talking about an assembly called locker_Apple_M1_64 — that is, designed for Macs with M1 processors. This file was noticed among the available versions of the malware — among which there is even an option for processors with the PowerPC architecture, released in 1992.
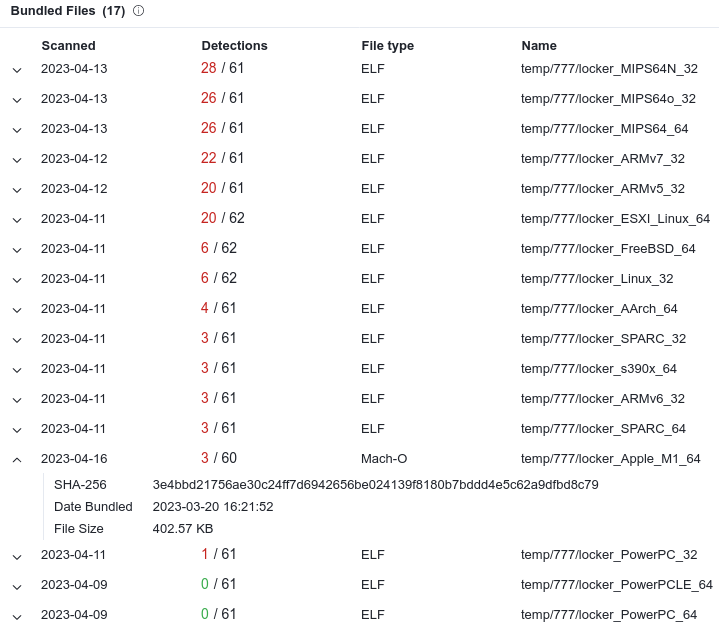
Later, screenshots of this LockBit build appeared from November 2022, but it was not possible to find any posts or messages about it since then. It seems that this data surfaced after the publication of MalwareHunterTeam on April 16.
After analyzing locker_Apple_M1_64, the authors of Bleeping Computer came to the conclusion that this is a test build, which in its current form is impossible (or at least very inconvenient) to use on macOS. It contains numerous references to missing components, mentions of file extensions and folders and Windows, which shows that the cryptographer is not ready for distribution and attacks on Mac.
At the same time, a LockBit representative gave Bleeping Computer a comment according to which the cryptographer for Mac is now "actively being developed" — which confirms that there is no threat to macOS users now, but this may change in the future.